Dear reader,
If you have come across the following page, you have probably been looking for a possible solution to your problem with Zepto Virus. Luckily for you, in the following article we are going to give you a detailed description of the virus that has recently been bothering you. In fact, Zepto Virus is considered one of the hardest pieces of malware to deal with and detect before it is too late.
Fortunately, we are going to share with you some prevention tips, general information about the possible ways of fighting this modern nightmare as well as a set of probably helpful removal steps.
Ransomware in general
Ransomware represents malicious software, which is programmed to stop the infected users from accessing some of their files. It actually puts something like a password to prevent the users from reaching their data. Typically, this encryption consists of two parts – a private one and a public one. The public one is given freely to the victimized user, but a ransom is demanded for receiving the private part of the encryption key. Usually such payments can be done through various payment methods online like Bitcoins. Nevertheless, even provided that the victim user indeed pays, it is not guaranteed that the blocked files will be decrypted. To top it all, the requested amount of money for ransom may greatly vary from $24 to more than $700 and is a subject of constant change, as the hackers may threaten to increase the sum in case it is not paid on time. In addition to that, you should always bear in mind the fact that completing such a ransom payment might also be seen as a criminal activity. Unfortunately, the only consequence of paying may not be the decryption of your lost data, but only the greater motivation for the hackers to go on with their harassing and blackmailing strategies.
How does Ransomware get distributed?
You may be unfortunate enough to be faced with the Ransomware threat via plenty of methods and means. Such a scenario may become real, when you unknowingly download the virus by visiting already compromised web pages or as a result of a payload, which may be either dropped or downloaded by other malware. However, the most common way of catching Ransomware remains by opening a contaminated email or any of its infected attachments.
Beware, as Ransomware never comes on its own – it is usually aided by a Trojan. Remember to get rid of this virus, too, after you have found a successful solution to your Ransomware problem.
How does Ransomware kidnap your PC?
Immediately after it has been executed on the computer, this malware is likely to either lock the computer screen or proceed with the encryption process of your most regularly used data. In the first possible case, the Ransomware usually displays a notification on the monitor that stops the infected user from using their system. Despite that, in most of the cases, you have been unfortunate enough to catch the other more common version of Ransomware, it will encrypt your most often used data like documents, spreadsheets and other important data.
Zepto Virus and how it affects your system
You become aware of the fact that you have to deal with malware as soon as you receive the notification for the ransom. However, is it possible to perceive the threat and its effects before Ransomware is done kidnapping your data?
If you have become a victim of this virus, you are likely to experience an obvious slowdown in the performance of your system as a whole. In fact, the possible slower performance is dependent on the speed and the power of your processor. However, more or less obviously, the encoding Zepto Virus tends to perform usually takes time and incredible amounts of resources. If you have noticed something that matches the explanation above, you are supposed to open and check your Task Manager for the activity that is taking up the most RAM. Among the first processes in the list you will find the suspicious process that Zepto Virus undertakes. What you should do after that is to shut down your PC as soon as possible. Then you are not supposed to start it before you have found a solution or have consulted a specialist.
Is it wise to pay or is it wiser not to pay?
To be precise, this question is asked more and more frequently, as more and more people nowadays have to deal with this virus. The bad news is that we can give you no concrete advice, as there is no correct answer to this question. You will have to make the tough decision on your own. However, it is never clever to do business with criminals of any kind, including the cyber ones. This can only encourage them to hijack more computers. Keep in mind that whatever you do, no matter how much money you give and how much effort you put into recovering and accessing your encrypted data again, that may not happen. Paying off the ransom and removing the virus do not equal decryption of the hijacked data and taking back the control over it.
Good luck!
Welcome to our Zepto Virus removal instructions. This article intends to help you remove Zepto Virus from your system and is designed to work for all Windows versions.
Zepto Virus Removal
![]()
Reveal Hidden Files. If you don’t know how to do this, ask us in the comments.
![]()
![]() => Search=> Copy/Paste “notepad %windir%/system32/Drivers/etc/hosts” => Enter.
=> Search=> Copy/Paste “notepad %windir%/system32/Drivers/etc/hosts” => Enter.
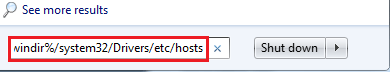
If you notice other IPs different from the localhost IPs – you might be in danger!

Ask for additional help in the comments.
![]() Right click on the Taskbar => Start Task Manager.
Right click on the Taskbar => Start Task Manager.
Navigate to Processes.
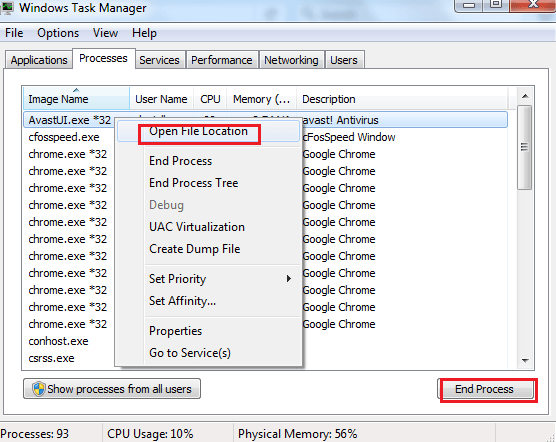
Locate any suspicious processes associated with Zepto Virus. Right click on the process = > Open File Location => End Process = > Delete the directories with the suspicious files.
![]()
![]() => Search => Type:
=> Search => Type:
- %AppData%
- %LocalAppData%
- %ProgramData%
- %WinDir%
- %Temp%
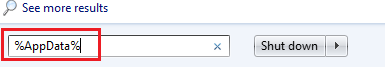
Hit Enter after each new search. Check each Folder and delete recent entries.
![]() Get Your Files Back!
Get Your Files Back!
The only way you can do that is by backpedaling to a moment when you were not infected. You can achieve this in one of two ways:
- System Restore.
 => Search field => Type System Restore => Enter.
=> Search field => Type System Restore => Enter.
Choose a Restore Point.
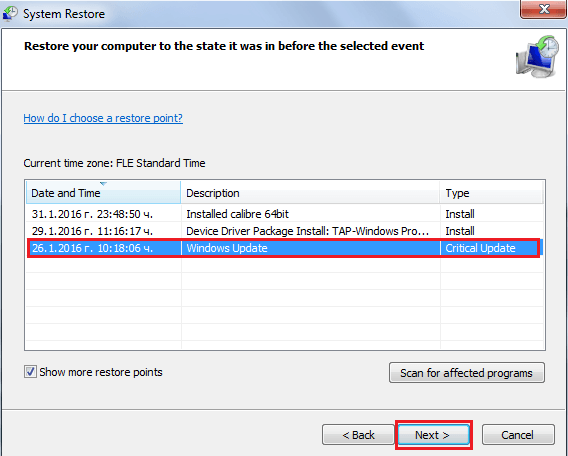
Click Next until the process has been completed. - Google and Download a Program called ShadowExplorer. Install and open it => Choose the Drive letter (C:, D:, F:, etc.) and date you want to restore information from => Right click on the files you want restored => Export.
If you run into any trouble – ask us for help in the comments section!





Leave a Reply